The state of mobile app security: How to tackle the challenges?
You will strongly agree on this:
Mobile devices have become THE essential part of our lifestyle.
And it’s not just on the personal front, mobile devices are transforming businesses in a multitude of ways. It is a major revenue driving force of social, enterprise, utility and other consumer businesses.
Our work, food, friends, sleep cycles and just everything else is extremely dependent on them! Do you agree?
Let’s talk about some numbers first:
The growing demand of mobile apps
According to the 2017 US Mobile App Report by ComScore, 18-24-year-olds dominate the smartphone app culture by spending almost 2/3rd of their digital media time on mobile apps alone.
Here’s another one:
Statista forecasts that by 2020 mobile apps will generate around 189bn US dollars in revenue via app-stores and in-app advertising.
With this rising number, mobile app developers are constantly facing the increasing demand to build apps at a faster rate.
More demand and supply and even more app security:
As the demand for apps has risen, so have the malicious attempts of the dark world. Now this is a major concern.
And the proof lies here:
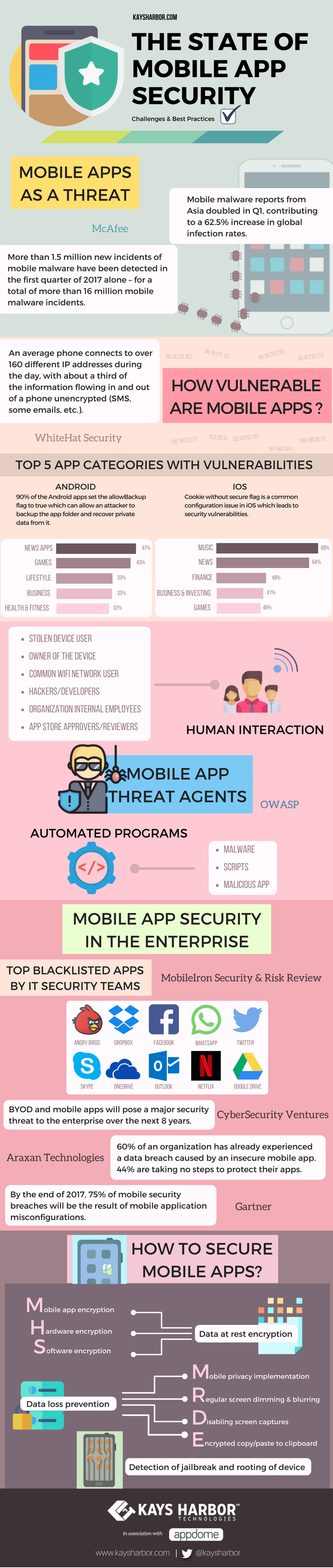
47% of news apps on Android and 69% of music apps on iOS have been reported to have vulnerabilities so far. Not only PCs but also mobile devices are coming under the scanner of ransomware, a new generation of malware that has no boundaries.
Infact, according to the mobile security report by CyberSecurity Ventures, BYOD and mobile apps will pose a major security threat to the enterprise over the next 8 years.
Failing to address this issue at your enterprise can lead to severe financial losses and privacy breaches. That’s why, there is a dire need to shift the attention towards making preventive measures against cyber-attacks on personal as well as enterprise mobile devices.
You can also consider choosing the cloud mobile integration services by organizations like Appdome that help in solving these mobile app data protection and embed the necessary security suite. Their team highlights the following 3 must haves to build a secure mobile app:
Best practices to ensure mobile app security
1. Data at rest encryption
According to a research conducted by HPE, 75% of applications do not use correct encryption methods for the storage of data from the mobile device. Implement data at rest encryption to ensure that the data which is not moving (over the network) is safe in any physical storage.
Often the data captured and generated by apps is not encrypted by design. This can be secured by:
-
Mobile data encryption:
Mobile app data ranges from personal credentials, photographs, texts, business emails and other confidential information. This data is prone to being lost or stolen. This data can be stored in an encrypted form with gated permissions for the app to access it.
-
Hardware encryption:
Hardware encryption encrypts the entire filesystem, which includes the OS and user data while it’s in flash memory. It is then decrypted in main memory when in use. However, it’s not always in use and even when it’s enabled, users often want more protection.
-
Software encryption:
Software encryption encrypts a specific app such as a CRM tool, a social app for the workplace or groups of apps like email, calendaring and contacts. Even with hardware encryption in place, software encryption adds another layer of security and the two should often be used together.
What are the challenges faced in data at rest encryption?
When developing an app that needs encryption, developers often face variable data structures and multiple choices like the type of encryption to use and meeting regulatory mandates like FIPS. Usually, encrypting three different data structures requires three entirely different approaches to data at rest encryption.
Encrypting certain data structures compromises with the performance and speed. The challenge lies whether the speed of the app should be compromised or not. Due to this, one or more of these data structures get left out for performance, usability and other considerations.
2. Data loss prevention:
Mobile data loss can take many forms and is a threat to mobile security and privacy. OSWAP has categorized mobile threat agents into 2 such categories:
- Human interaction
- Stolen device user
- Owner of the device
- Common WiFi network user
- Malicious developer
- Organization internal employees
- App store approvers/reviewers
- Automated programs
- Malware
- Scripts
- Malicious app
Even a stranger at the airport who glances over your shoulder at your mobile screen could be responsible for your mobile data loss. Learn more from the Ponemon Institute study on shoulder surfing.
Fortunately, there are ways to mitigate these issues with privacy controls.
-
Implement mobile privacy
Privacy and security are closely linked to mobile devices and both need to be considered when creating apps. Developers often defer, delay or ditch adding mobile privacy features.
-
Mobile screen dimming and blurring
Screen dimming and blurring helps protect from shoulder surfing. When a user switches screens between apps, the mobile device will present the screen in a thumbnail. If not obfuscated in some way, that thumbnail could display sensitive information to the viewer. By creating a blurred or dimmed thumbnail for an app screen, the screen will be automatically blurred or dimmed when the device takes a screen capture as part of app switching or home screen usage process.
-
Disabling application screen captures
Users often take a screen capture of what is displaying on an app for later reference. Unfortunately, this can put sensitive data at risk, especially if photos are automatically backed up. Because of this, many organizations prefer that this capability be disabled for their apps.
-
Copy and paste protection
Many organizations are concerned with users copying sensitive data out of an app and pasting it into another app such as email or a browser via the device clipboard. It would be wise if everything copied and moved into the clipboard from your app is encrypted.
3. Detection of jailbreak and rooting of device
Jailbreaking and rooting of mobile devices is a pretty common practice. Globally, depending on whose stats you believe, somewhere around 10 percent of iOS devices are jailbroken and 27% of Android devices are rooted. It’s virtually impossible to prevent rooting and jailbreaking. When it comes to jailbreaking and rooting – prevention can’t be the goal. Instead, the goal should be detection and response.
Organizations should have policies to disallow access or alert when mobile devices that are jailbroken or rooted interact with their assets. From a practical perspective, most developers and organizations opt to alert a user or administrator if a jailbroken or rooted device is detected rather than exiting the app.
Carefully considering these security mechanisms can help keep malicious code at bay and secure confidential information.